
Configuring Burp Suite With Android Nougat 2020
So I wanted to try out Web App and Android App penetration testing the first software I was introduced to was BURP Suite, best in class industry standard tool for Penetration Testing.
Background
It had crossed me as I remember when Pathao App was accused of stealing personal data (Accusation was proved and necessary actions were taken) BURP was used for testing. So I went on a journey to configure BURP for android.
In Android Nougat, we’ve changed how Android handles trusted certificate authorities (CAs) to provide safer defaults for secure app traffic. Most apps and users should not be affected by these changes or need to take any action. The changes include:
https://android-developers.googleblog.com/2016/07/changes-to-trusted-certificate.html
Ads Disable Temporarily
That was the most painful task to do as though burp was easy setup the main problem was to get the certificate working inside Android 7+. I had a Android 9 and the problem with this version (I said problem but its a benefit if you are a general user) was that it did not allow for CA Certificates that are user installed to allow proxy connections that Burp needed in order to work.
The phone I used was a Xiaomi Mi 6x Rooted with Magisk, it is currently running MIUI 11.2 Android Version 9 - Pie.
As expected I followed all steps denoted in their website: Link, I got through some of the basic steps. Then came the most painful part getting the certificate to android. The Steps over at: Configuring Burp Suite With Android Nougat are really great but the current needs are different as android is ever evolving.
Install the Burp Suite CA as a system-level CA on the device. My recommendation for the easiest solution, but does require a rooted device. Also added benefit of not having to set a lockscreen PIN 🙂
Basic requirements
Though I say basic but its the most crucial element to succeeding in solving this simple problem.
The first thing you will need is an android device, it has to be rooted. (Use Magisk as it simply the best i have seen so far due to its ability to hide from apps)
Second you need a Linux Machine - I use Kali Linux on a virtual Machine to do my task.
Steps
Step 1: Start Burp Suite and add a new proxy listener. Make the proxy listener a Specific Address

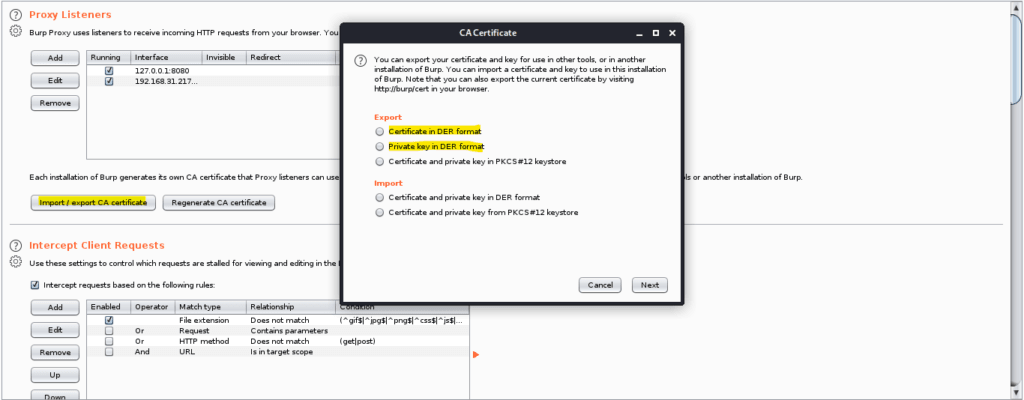
Step 2: Export the Certificate and the Certificate KEY
First Click on Import / Export Certificate then first click on export in DER Format and Save file as cacert.der (you can use any name but I am using this and will be continuing to use this as reference name) then again do the same but this time select private key in DER format and save it as cacertKey.der . I stored them at root for easier manipultaion.
Ads Disable Temporarily
Step 3: Open Terminal and Use the following codes
openssl rsa -inform der -in cacertKey.der -outform pem -out cacertKey.pem
the above code will tell openssl to change the key from DER format to PEM format. We need this in order to sign the conversion of our cacert.der certificate to cacert.pem but the the key.
openssl x509 -inform der -in cacert.der -signkey cacertKey.pem -days 730 -outform der -out cacert2.der
The code that worked next would be telling openssl to create a new certificate in der format and save it as cacert2.der this is done in order to keep the original and the edited version. The code above also changes the validity of the certificate which is needed for apps to function properly. A typical certificate would last about 29 months so I gave about 730 days that is equivalent to 2 years or 24 Months. The signkey is our key we have converted this ensures that we are able to import it back to burp as we changed the date of issue and expiry. Next, we will convert the original to a pem certificate.
openssl x509 -inform der -in cacert.der -signkey cacertKey.pem -days 730 -outform pem -out cacert2.pem
This is needed for the android system which reads pems as a valid certificate. After the certificate is generated we will use the below 2 codes
openssl x509 -inform pem -in cacert.pem -subject_hash_old |head -1 cp cacert2.pem <Hash>.0
The first code will provide a result such as below:
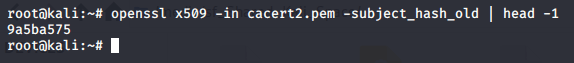
The <Hash> for me is 9a5ba575. Up execution of the next code a new file will be generated with the hash and extension of zero.
Step 4: Copy the Cacert2.der and the <hash>.0 file over to android with any tools or method of your liking.
Ads Disable Temporarily
Step 5: Copy the <hash>.0 to the folder /system/etc/security/cacerts/
my preferred file manager for this is Mixplorer.
Step 6: Follow the steps over at Burp Suite - Link, use the file cacert2.der for the task and then proceed to next step
Step 7: Import into burp the Cacert2.der using the old der key.
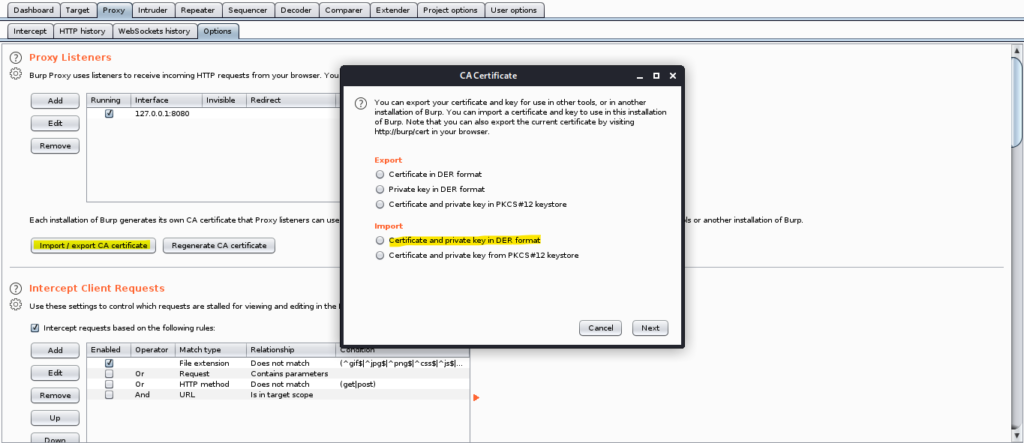
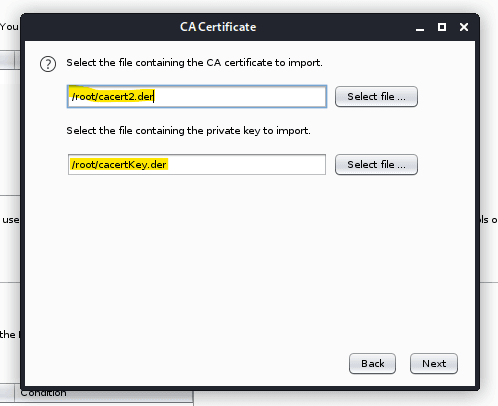
Viola All steps complete now you can start using BURP Suite with your android device.
Raw Codes
openssl rsa -inform der -in cacertKey.der -outform pem -out cacertKey.pem
openssl x509 -inform der -in cacert.der -signkey cacertKey.pem -days 730 -outform der -out cacert2.der
openssl x509 -inform der -in cacert.der -signkey cacertKey.pem -days 730 -outform pem -out cacert2.pem
openssl x509 -inform pem -in cacert.pem -subject_hash_old |head -1
cp cacert2.pem <Hash>.0Related Topics to Read
Backdoor Attack - 60 Million WordPress Sites at Risk
Ads Temporarily Disabled
